Every Access Group’s Role has its own set of Objects that permissions apply to. Previously, the permissions were defined, and now the focus is on selecting the Objects themselves. Objects can be assigned in three different modes, each described below along with its method of application:
-
Simple: All Objects within DCT.
-
Scoped
-
Tags: Objects with matching Tags.
-
Direct: Objects manually assigned.
-
-
Advanced Scoped: Objects are assigned directly on the permission action (like Read Bookmark, Edit Bookmark, or Delete Bookmark) using Tags or Direct Assignment.
The first two modes—Simple and Scoped—are covered here. Advanced is easier to understand afterward and can be a good self-guided next step. Before diving in, make sure your DCT server has a handful of objects, such as Bookmarks or VDBs.
Simple
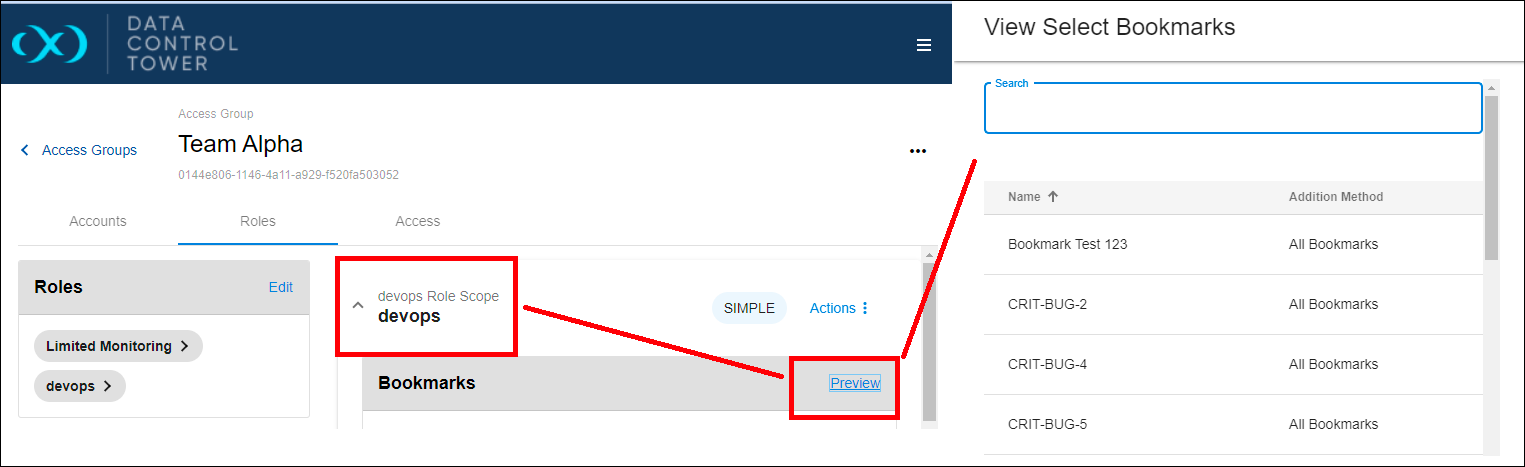
If you have two Roles assigned to your Access Group, for example “devops” and “Limited Monitoring,” both start in the Simple mode by default. To see how broad this Role’s coverage is, select anywhere on its row and click the Preview button on the right.
Next, check the Preview list for Bookmarks, which shows every Bookmark the Role can access and how the permission is applied. This is an easy way for Administrators to confirm access without switching logins. Since this is a Simple scope, every object is included, so the preview might not look especially surprising. In the next section, the Role will be refined further.
If no objects are listed in the Preview widget, it could be because:
-
Engines are not connected.
-
No DCT-only objects (like Bookmarks or VDB Groups) are created.
-
Permissions are being enforced correctly (and possibly blocking access).
Scoped - Direct
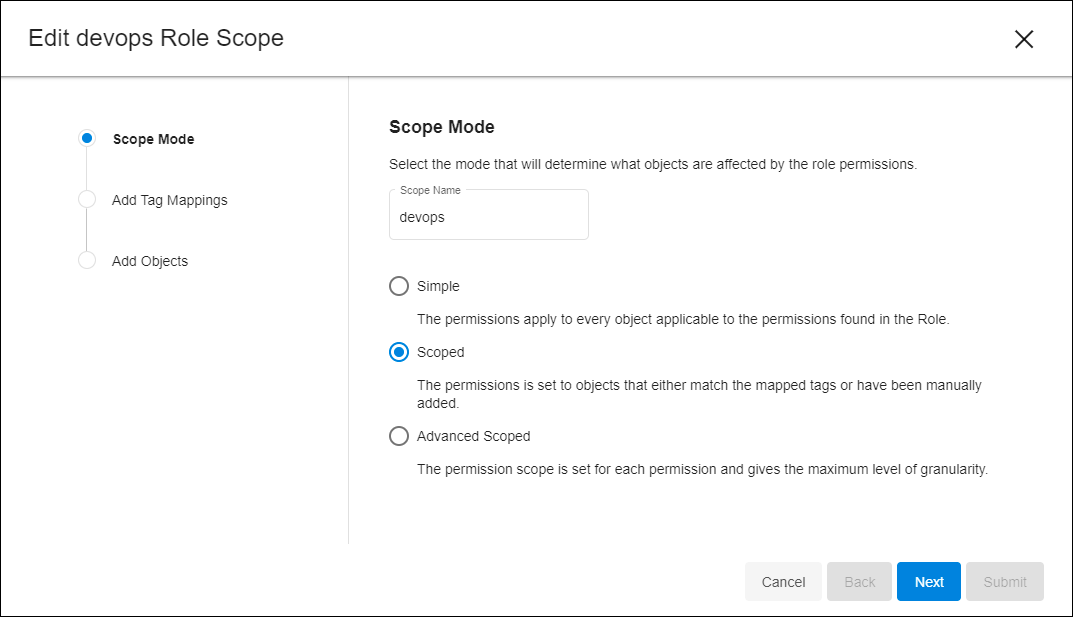
Switch the mode to Scoped to target a subset of VDBs. On the Access Group > Roles tab, select Action > Edit for the Role you want to change.
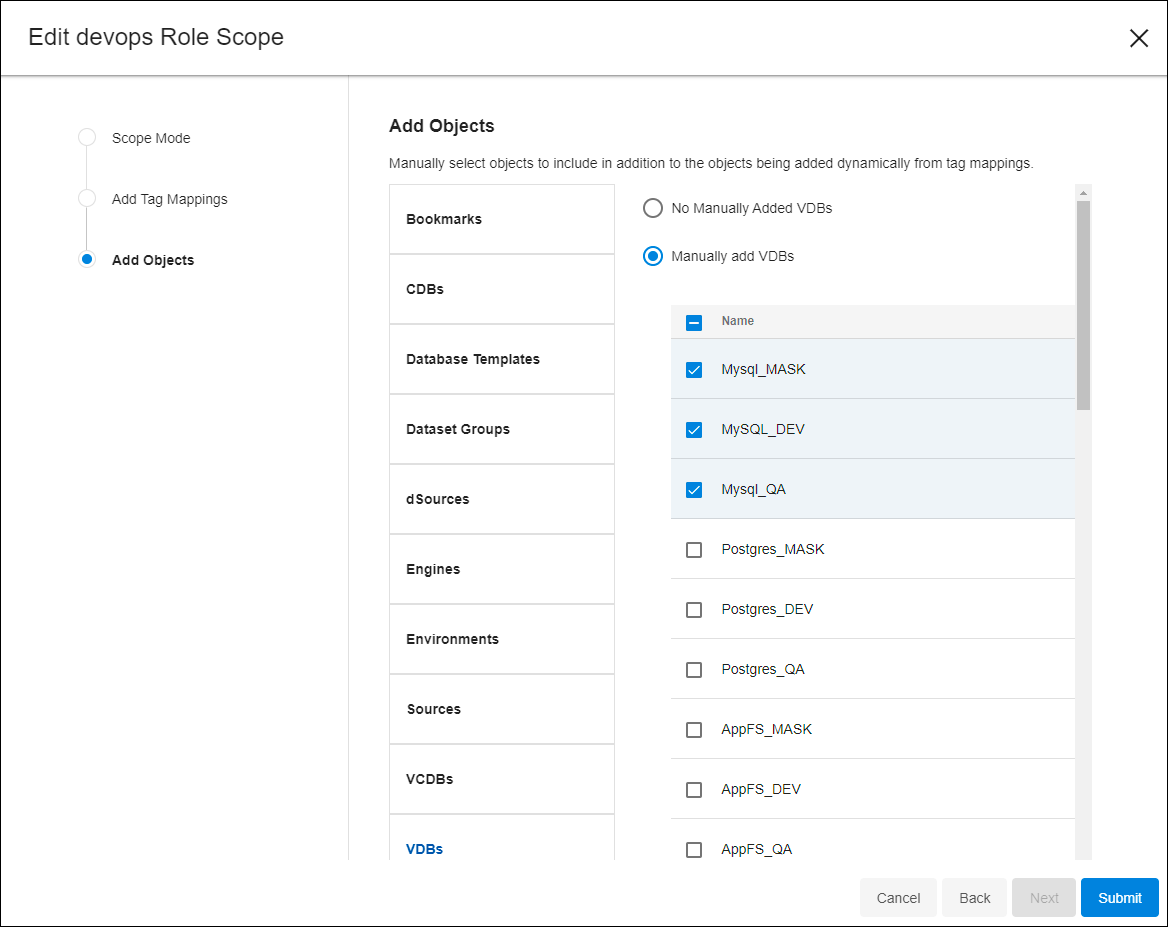
A new wizard will appear showing the Simple, Scoped, and Advanced Scoped options. Choose Scoped, skip Add Tag Mappings for now, and select Next to reach Add Objects. You will see a list of objects available to DCT, where you can manually assign specific ones.
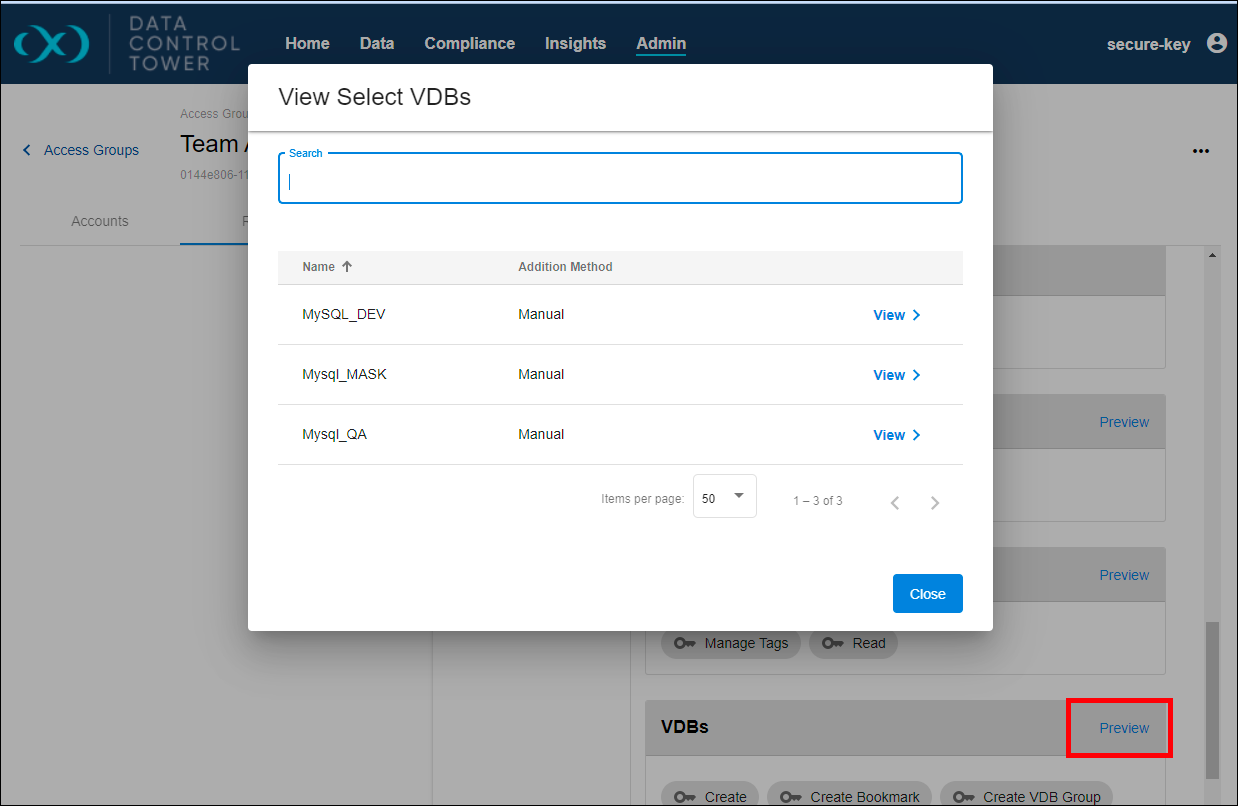
Scroll down to the VDBs section, choose Manually add VDBs, and pick a couple from the list on the right. Feel free to add other Objects as well. When finished, click Submit. This changes the Role’s mode from Simple to Scoped. Verify by opening the Role’s row, finding the chosen Object Type, and selecting the Preview button for VDBs.
You should see the same VDBs you selected. If you want to verify them directly, login as another test user and confirm the permissions.
Note: Any additional Roles or Access Groups assigned to the same user might affect overall visibility. If you test this, make sure no other permission set is influencing your results.
Scoped - Tags
While Direct Assignment is great for early onboarding or one-off needs, tagging Objects and Roles is a faster way to handle permissions at scale. By assigning matching Tags to Objects and Roles, you can automatically grant or restrict access. This is often the recommended approach for robust production setups.
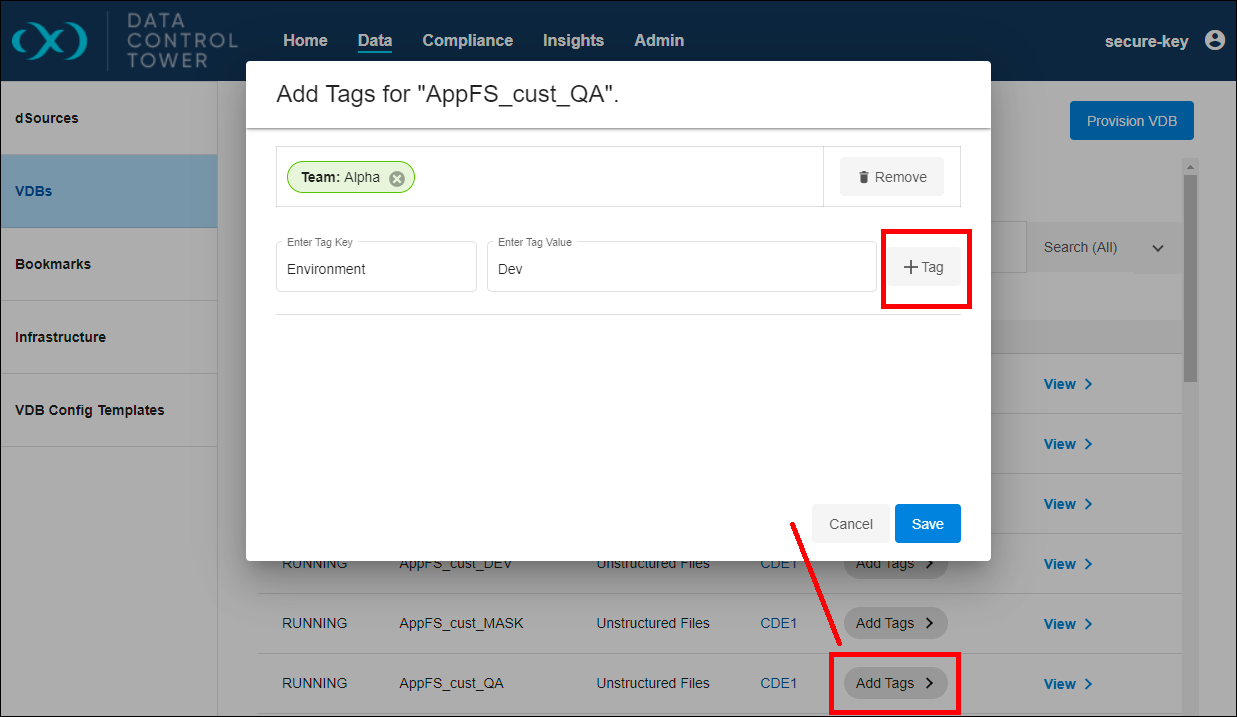
First, open the top-level Data > VDBs tab (or any other tab with available objects). Find a test object and click Add Tags.
Use a Key-Value pair that suits your organizational method. For instance, you might choose something like “Team: Alpha” or “Environment: Dev.” Assign tags to a few different objects for variety. This helps organize your Delphix environment and govern access more easily.
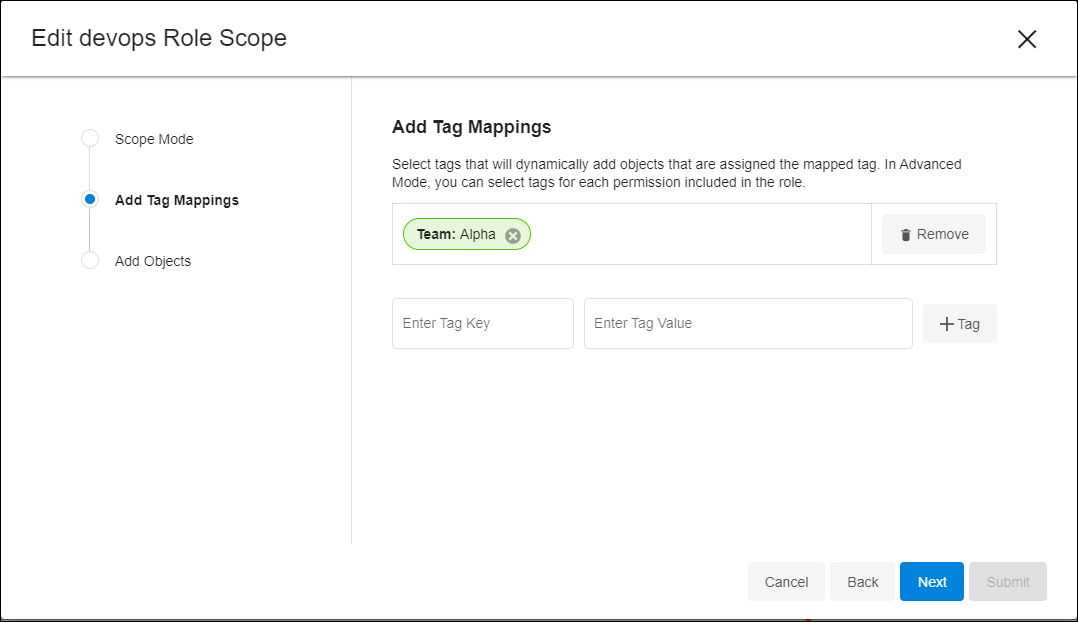
Next, put these tags to work in the Access Model. Go back to the Access Group you are testing, open the Roles tab, and edit the Role you updated previously. Since Scoped is already selected, click Next but stop at Add Tag Mappings. Assign one or two of the same Key-Value pairs you just used.
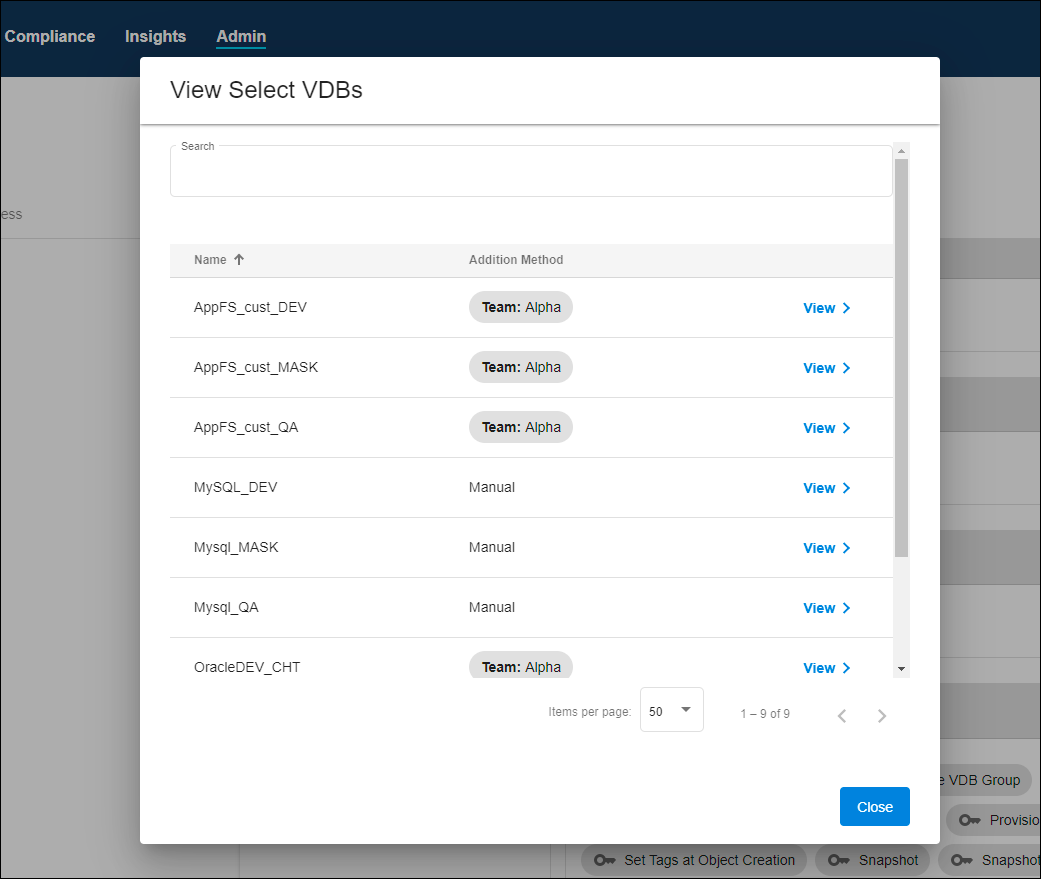
This automatically grants the tagged Objects to the Role, applying the permissions defined by that Role. Verify the tags by completing the form and using the Preview button again.
You may notice a mix of objects assigned through both Tags and Direct assignment. At this point, it can be helpful to experiment by adding and removing tags from different Roles and Objects to see how flexible the ABAC model is. If you want a deeper dive into Tags, check out the relevant documentation.